Dear participant,
Thank you for taking part in this challenge!
pCloud Crypto is a service, dedicated to providing ultimate file security to users worldwide. We are confident that we have built a client-side encryption software that nobody can hack. Now we are willing to give $100,000 away (or the equivalent in Bitcoin) to anyone who breaks into it. By participating in our challenge you help us build even a better and more reliable service, and we truly appreciate that!
Before starting your participation, make sure you read and fully understand the following terms and conditions.
Terms of Participation in the pCloud Crypto Challenge
1. Challenge period
The pCloud Crypto Challenge will be open until April 4, 2016. You can use all this time to try and hack our client-side encryption. You can make numerous tries.
2. Credentials
When you enter the pCloud Crypto Challenge, you will be given the following credentials:
- Password
You can use these to log in via any device - desktop, web, and mobile.
Important: Participants from Round 1 will receive the new Challenge credentials automatically by email.
These credentials are general and open a common pCloud account, used for the challenge by all participants. This account gives you a read-only access. You will not be allowed to upload anything to it, but you can view and examine everything that is within the account.
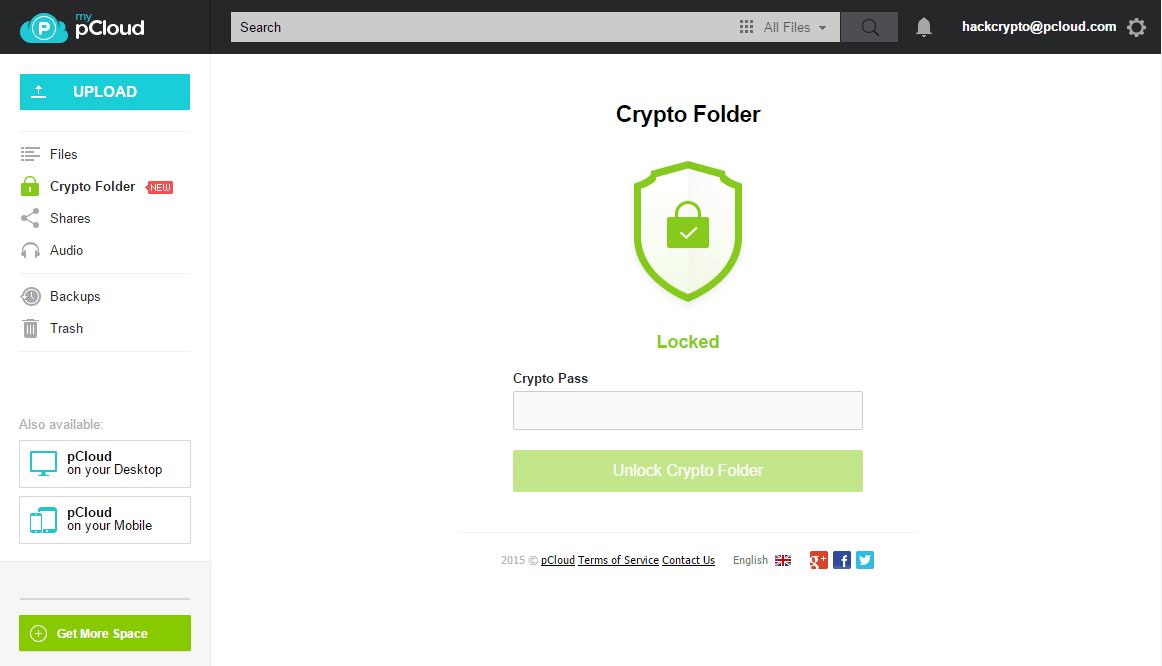
After you enter the Challenge account and click on the "Crypto Folder" in the left menu, the screen above will be shown.
This challenge account will contain a client-side encrypted folder, just like any pCloud account. We have placed and locked certain files in it. Your task is to hack into the encrypted folder and decrypt the data that is inside.
For the Challenge you can use the Source Code of pCloud Crypto for Mobile. Download it from here.
Note: You will not be allowed, and you will not have the rights, to change the common pCloud account password.
3. What is considered Successful Hacking
As mentioned above, the challenge account will contain a Crypto folder with a number of encrypted files inside it. Your task is to hack into the encrypted folder and decrypt the data, and send it to us in decrypted state at cryptochallenge@pcloud.com. Your hack will be considered successful only if, besides the decrypted files, you also send us a detailed explanation of your hacking approach, so you can prove that you have used a particular methodology to break into the folder.
Note: In case of multiple hackers using one and the same methodology, only the first one to send us their detailed explanation will be given an award. Any following hack, if proven to be performed with a different methodology, will also receive the specified award.
4. Exclusions
pCloud uses its real platform for the challenge, so, when participating, remember that you are playing on the real arena! In this sense, no hacking of any other aspects of the service, besides pCloud Crypto, is allowed. Any user, who performs a hack, outside the scope of the contest, will be banned and excluded from the challenge. Exclusions may include, among others:
- DDoS attacks
- Hacking other users' accounts
- Random guessing of the Crypto Pass
- Preventing other users from participation
- Hacking any part of the pCloud platform, unrelated to the challenge
Note: Reporting of any bugs/problems, unrelated to pCloud Crypto and/or the pCloud Crypto Challenge, is highly appreciated, but it will not be rewarded with a monetary award.
5. Award
If you successfully hack (see clause 3 above) into the encrypted folder and send us its content in decrypted state plus an explanation of your hacking methodology, you will get a $100,000 award (or the equivalent in Bitcoin).
6. Award payment
The payment of your award will be performed in two stages:
1. Half of it ($50,000 or the equivalent in Bitcoin) immediately after approval of hacking.
2. The other half ($50,000 or the equivalent in Bitcoin) 3 months (90 days) later, upon successful fulfillment of the non-disclosure agreement (see clause 7 below) on your part. Upon payment of the second part you will also receive public recognition by pCloud for your successful hacking.
7. Non-disclosure
By entering this challenge you agree that in case of successful hacking of the pCloud Crypto folder, you will not publicly disclose any information related to it for a period of 3 months (90 days) as of the day of confirmation of successful hacking. After expiration of this period, pCloud will publicly announce your achievement and you will get public acknowledgment for succeeding in the challenge. The second half of your award will serve as a warranty for non-disclosure. Note that you will not be granted the second part of your award if you publicly disclose any information within the aforementioned period.
8. How we use your data
The ways in which we use the data you provide to us, may include the following, among others:
- use your Personal Information for internal purposes, such as to provide you with the Site and Services;
- use your Personal Information to notify you about anything related to your participation in the pCloud Crypto Challenge, and to otherwise communicate with you about pCloud;
- use your email address for marketing purposes, by sending you newsletters or other email communication. If you have any objections about being contacted for marketing purposes, you need to notify us in writing or unsubscribe from our written communication;
- use your nickname and organization name for marketing purposes, such as to promote our campaign by stating publicly that you and/or your organization participate in our challenge
9. Other conditions
Your participation in the pCloud Crypto Challenge does not in any way violate other pCloud Terms of Service, such as pCloud's general
Terms and conditions,
Privacy Policy, and
Intellectual Property Policy. Any other use of the pCloud service and apps is subject to the aforementioned pCloud Terms.
Note: No fees or purchases are required in relation to your participation in the pCloud Crypto Challenge. It is completely Free!